This is a continuation of this original post in exploring the modifications that can be made to the OpenVPN source code to increase its overall performance: [post]
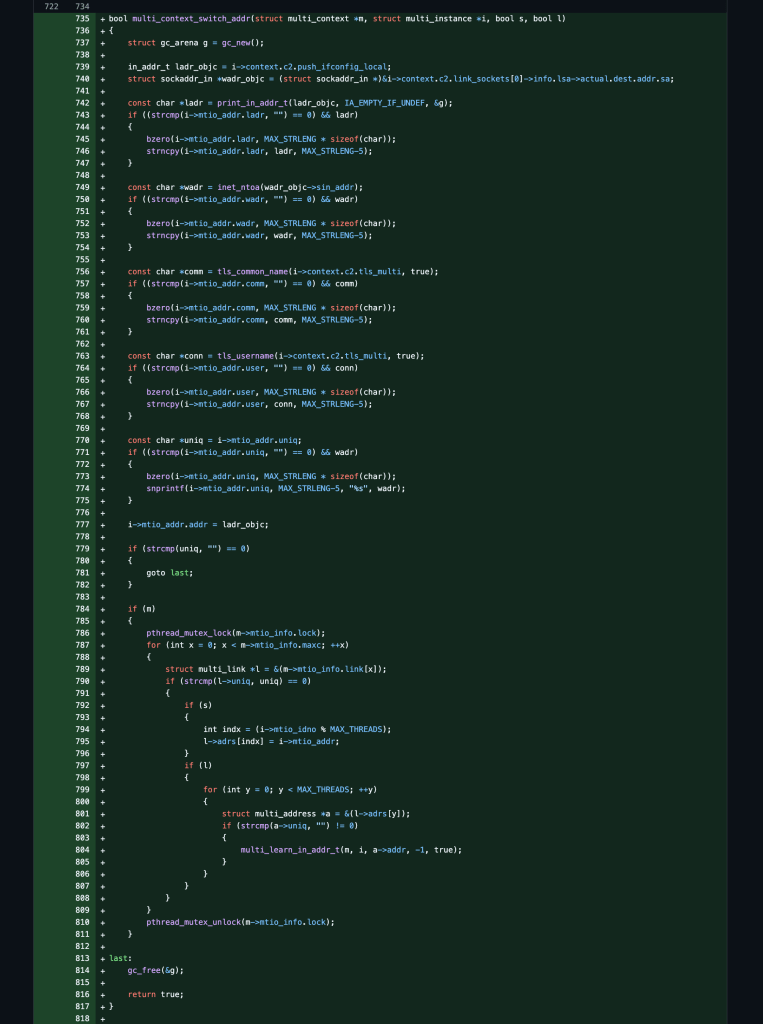
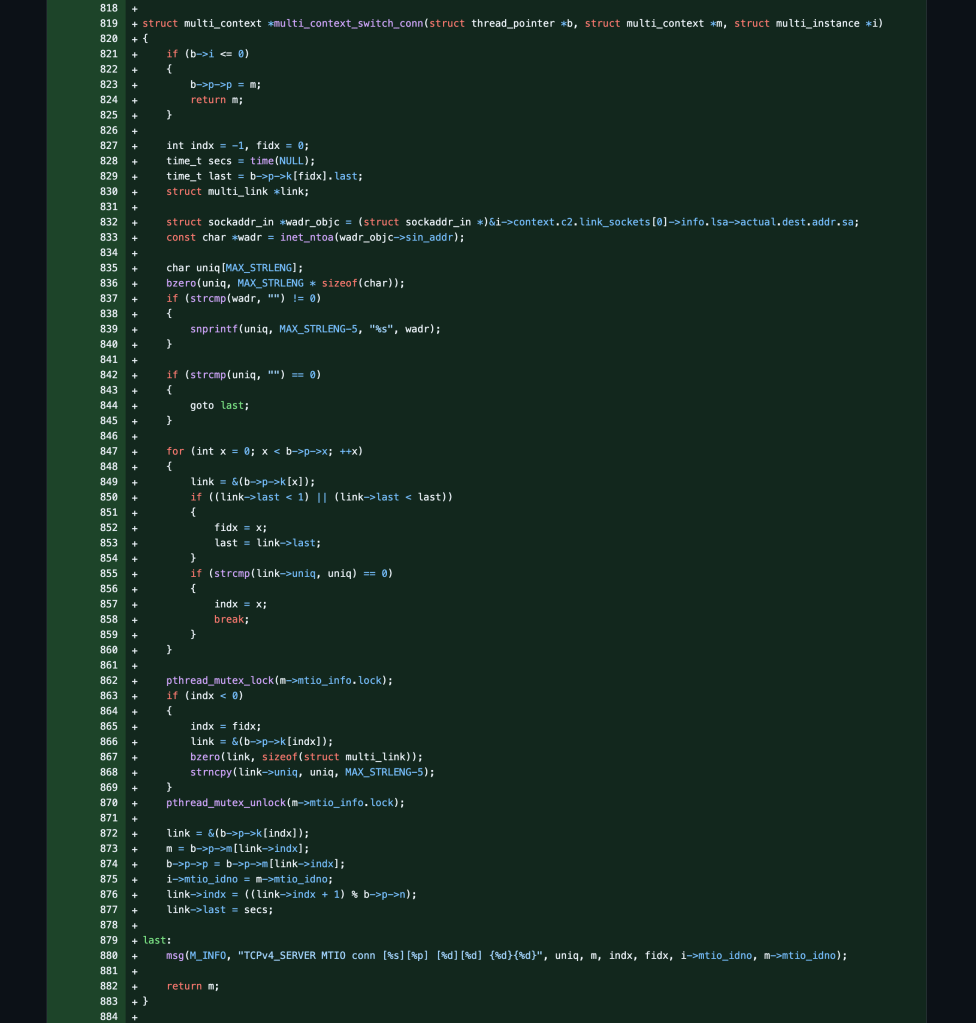
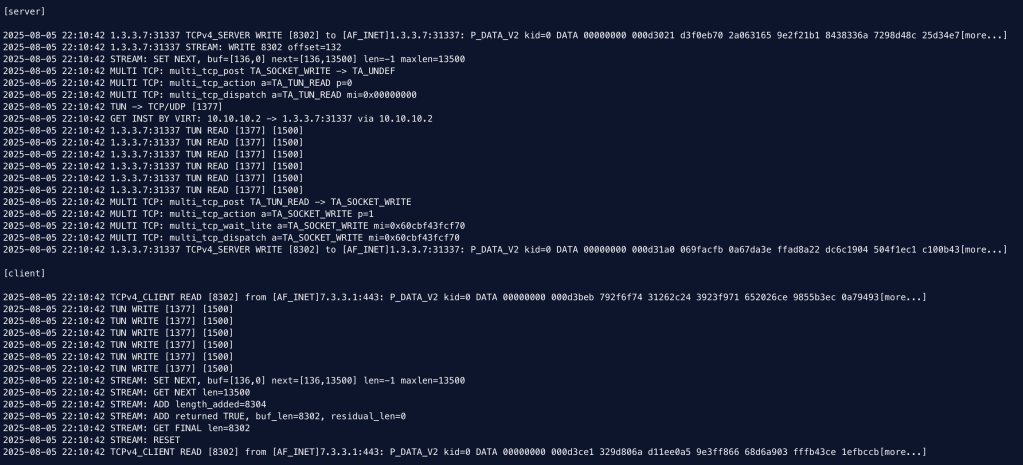
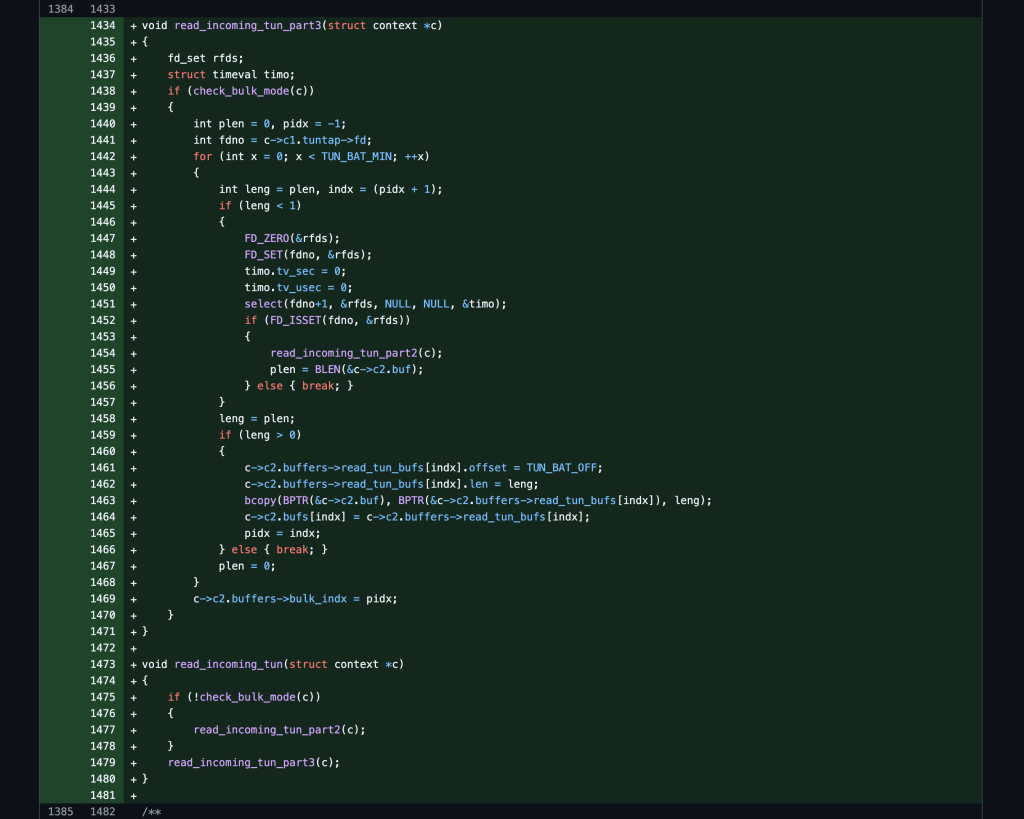
I’m still exploring how I can make this perform better and optimize the code more but I was finally able to build on top of the bulk-mode changes I had made in the last post and create a multi-threaded server and client model work together. It was tough to do because of the complexity of the code as well as not interfering with the TLS connection state variables and memory along the way.
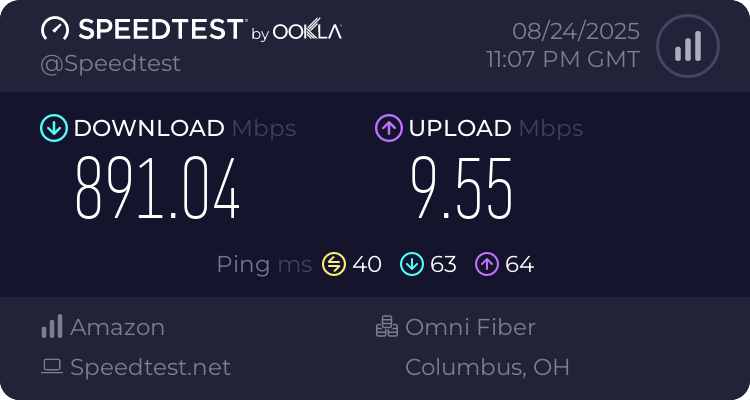
I was able to make the code spin off 4 threads which both share a common TUN interface for bulk-reads and then create 4 separate TCP connections to each perform a large bulk-transfer. The server will load balance the dual connections from the client across the threads based on the connecting IP address. I am also running 4 VPN processes with 4 TUN devices and using IP routing next hop weight to load-balance the traffic between them.
Update: I just implemented an extra management thread that is dedicated to reading from the shared TUN device and bulk filling the context buffers so that they can all run and process the data in parallel to each other now in a non-locking fashion (6 x 1500 x 4 == 36,000 bytes)!
Config Tips:
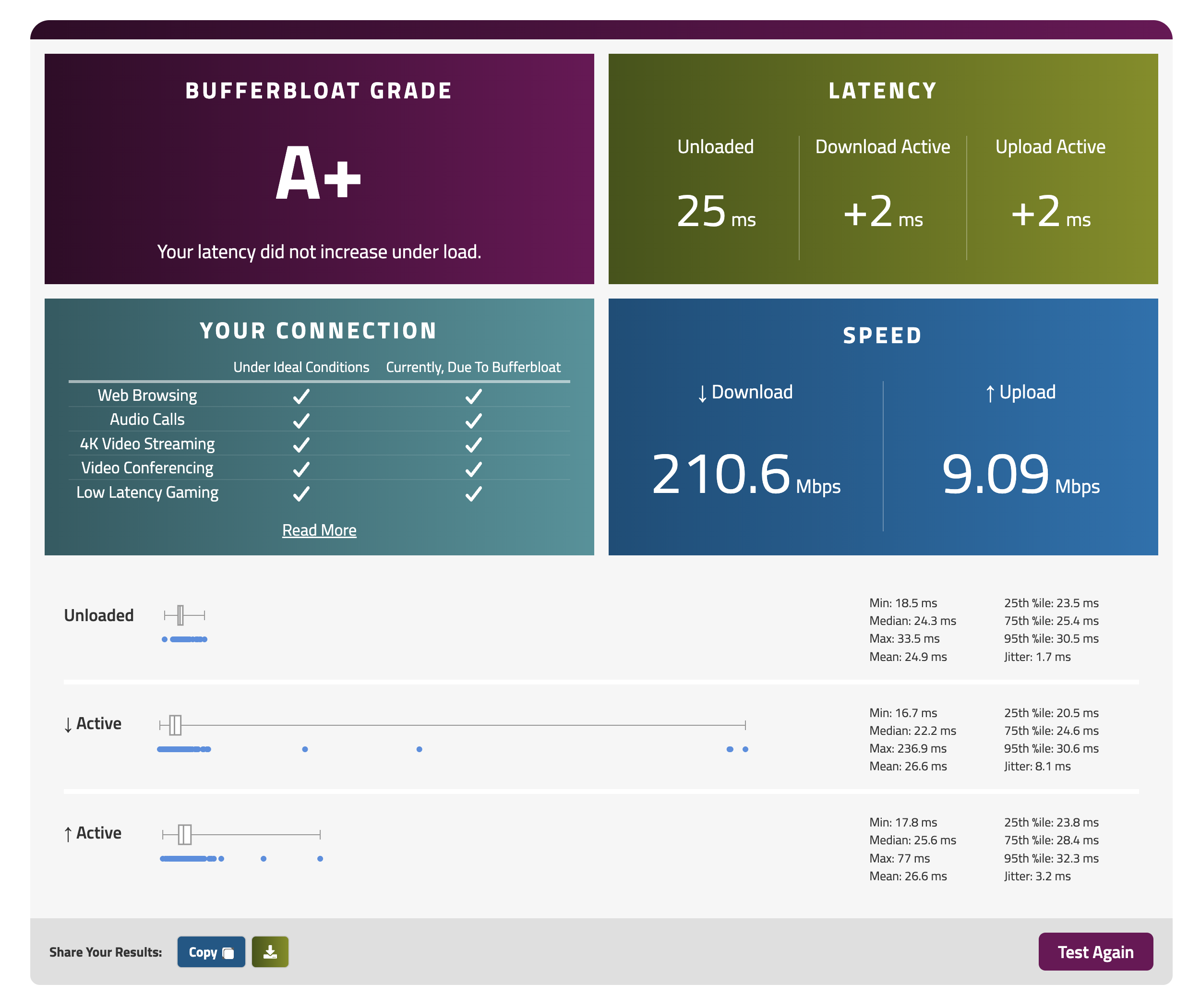
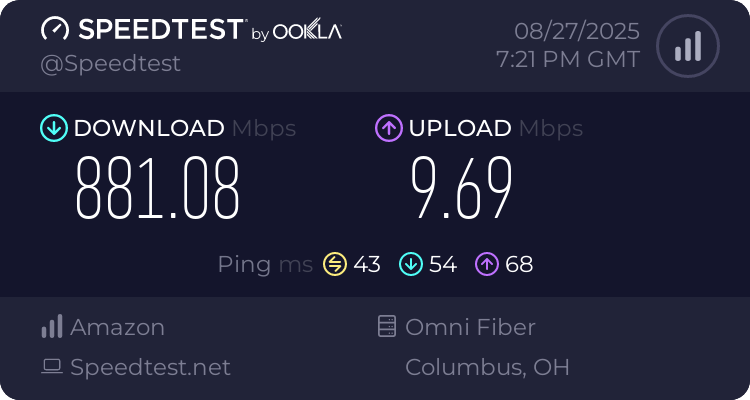
- Ensure that your VPS WAN interface has a 1500 MTU (my provider was setting it to 9000)
- Perform some basic sysctl network/socket/packet memory/buffer/queue size tuning (16777216)
- Set the TUN MTU == 1500 && TX QUEUE == 9000 (properly sized middle pipe link)
- Push && pull the snd ++ rcv buffer sizes from the server config to the client options (16777216)
- Use elliptic curve keys and stream cipher crypto (more efficient algos for the CPU)
- No more need for compression, fragmentation, or MSS clamping (–mssfix 0)
- Use a smaller timeout nftables values for fewer forwarded traffic table connection states (conntrack time_wait for udp/tcp)
Bulk-Mode ++ MTIO-Mode
~
~
~
~
Source Code: https://github.com/stoops/openvpn-fork/compare/bulk…mtio
Pull Request: https://github.com/OpenVPN/openvpn/pull/818/files
~